Source : Syafii, M,. 2004. Panduan Membuat Aplikasi Database Dengan PHP5 Postgre-MySQL-Oracle.Penerbit Andi. Yogyakarta.
Deface
You may have often heard or saw a site that has content not suitable. Obvious example is a site-education institutions (ac.id) to the index page of the official website of the picture or logo has been changed. Incident, in the world of hacking, called deface. Deface is an attack technique with the image or change the content of the website for a particular purpose. In fact, there are many factors that cause all of that. According to the analysis of the author, these factors are:
1. Operating system
If you intend to buy the domain and hosting, make sure that the operating system is safe and reliable in use, such as for example a Unix operating system variants. Please note that almost all of the hosting center are using Redhat Linux.
2. Programming Error
Low awareness of the website you are easily exposed to deface. For example, the error in using the user management in MySQL, but the data show that the user is able to perform SQL delete, insert or drop. This is the common mistakes that seemed as a habit that can not be abandoned. If you compile a program that uses a web-based MySQL database then you should have a user that is able to select the command, if you are only a web show in the MySQL database server to the web. You can create new users that are only able to insert or delete command. Deface technique done with the action called SQL Injection.
Password Theft
Another thing is to be considered when creating web pages that have a user authentication system. You must create a program may be safe to include encryption. No password or data encryption so people can easily tap (Sniff) your data. Thus, the use of encryption is also very necessary.
Creating confusion in the Directory
Avoid making the directory easy to order and the name is known by other people. For example, almost all websites have a folder called images, include, or other similar folders. This of course should be anticipated so that if users try to access the way, we already have a preventive action.
Error in File Include
When you read a lot about PHP3 tutorial or an older version then to insert a file in the PHP file is to provide the Include ( "db.inc"). In fact, if the *. inc files are called directly from the browser the contents of the file will be displayed. This means that someone can see the contents of your original file. If you just paste the file does not contain the usual problems. However, if you paste the configuration file contains a database then this will be dangerous.
Permissions for the folder contents
Keep other people can not easily find out each folder that you created in the order in the structure of the website. People can do it directly by typing the name of the folder. For example, if someone typing directly in the addres bar:
http://localhost/happy-holidays/images/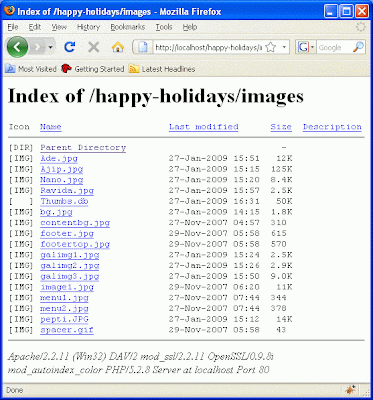
you can prevent problem like this by changing the configuration for httpd.conf in the folder under Apache, with the command to change or delete Options Indexes MultiViews tags below Directory. Another way that is easier to add in the index.php file in every folder that does not have the file index.php. So if someone tries to access directly the contents of a folder in the web then index.php file will be automatically executed, and the contents of the folder we will not appear as the image above.
Types and causes weakness of the Website
Posted by NanoTutor | Monday, March 02, 2009 | PHP | 0 comments »
Subscribe to:
Post Comments (Atom)



0 comments
Post a Comment